

Security Audit
- Category: Adversary Simulation
- Threat type: APT Adversaries
- Services Brochure: Download
Adversary Simulation
For those who are unaware, Adversary simulation is a type of Red Team engagement that mimics Tools, Techniques, Procedures and known threats to an organization. Globally accessible knowledge based of adversary tactics and techniques based on real world observations is collected under MITRE ATT&CK. This platform is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. Adversary simulation is completely different from Penetration testing as this simulation uses (TTP's) used by real threat vectors and test how the applied defenses act against them.
ATT&CK provides analytics and intelligence for the real world threat actors including various APT groups. Let us consider a simple example of a ransomware. Once a system gets infected with ransomware, the capabilities it uses to encrypt and spread over network uses certain commands. Threat emulation runs the similar checks and validifies the strength, logging and detection capabilities of applied active defenses.
Municipal governments, universities and private businesses have spent more than $144 million responding to the biggest ransomware attacks of 2020 (so far), spending on everything from rebuilding networks and restoring backups to paying the hackers ransom. Introduction of BYOD (Bring our own device) has introduced malwares to the organization as well.
Different forms of malwares are introduced using variety of Tactics, Techniques and Procedures (TTP's)
HOW ARE MALWARES DANGEROUS
Ability to encrypt files
Ransomware encrypts all the user data using strong encryptions like AES-256 with ciphers like CBC which is almost impossible to crack, thats why they are also used in transmitting confidential information.
Monetary loss
As per the Business Standard report the average cost of addressing the impact of such attacks in India costs an average of Rs 8 Crore. Some cases have also been observed where the hackers failed to deliever the decryption tool after payment.
Business downtime
Malwares have the special ability to spread over a network, on a successful impact it can easily take down entire network range, thus resulting in severe damage and business downtime.
Data breach and Reputation loss
Some malwares can go unnoticed sitting in an organization for upto few years, stealing data. This causes company to lose clients along with reputation loss.
SWITCH TO PROACTIVE PROTECTION
Our team of experts conduct tests with custom coded ransomware, and other malware samples are executed in our controlled environment that is a copy of your organization setup like domain policies, network settings and installed AV solution. The test is performed in our labs and sometimes on client location in a virtualised environment. Various ATT&CK techniques also known as Atomic tests are executed in this virtual environment to find the possible weak points, these tests are used by real threat actors in wild to achieve entry and persistence. Malwares of various catgories are also executed in this environment to observe the effectivess of your implemented security policies. This includes tests for both file and latest fileless malwares.
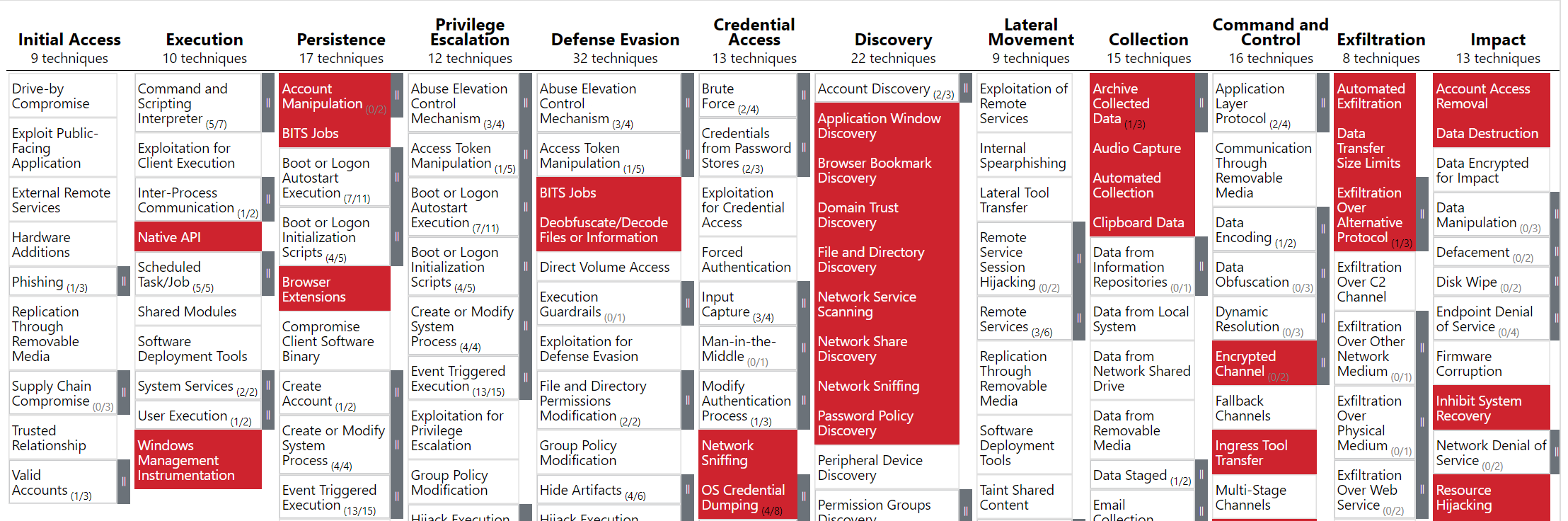
This test provides an enhanced view over the damage that can be caused in case a malware hits the environment by exposing the vulnerable areas. The below image shows categories of the types of tests performed.
DELIVERABLE
The test reveals the vulnerabilities in the security solutions and the implemented configuration settings. Recommended settings are then suggested to harden the security. Test report delievers tests performed, detection rate of security systems, vulnerabilities in existing configuration, followed by the changes that need to be made to harden the overall security posture.
QUICK LINKS
Contact
Got Questions? We are just an email away!
